The scary reason why you should never share phone chargers
Don’t let hackers drain your data.
A professional hacker has revealed the malicious technology hidden within phone chargers that can “cause havoc” on personal devices.
Ryan Montgomery, who is hired by companies to test cybersecurity flaws in their network, took to Instagram to discuss the potential dangers of using charging cables of unknown origin.
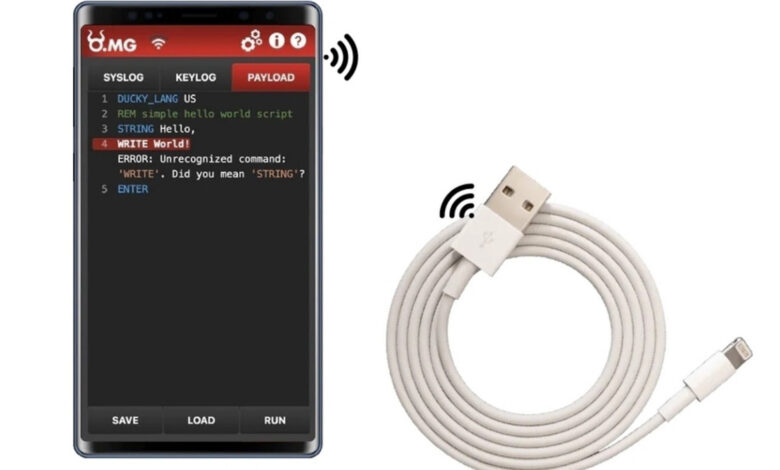
When he took an “ordinary-looking cable” — which is “fully functional” and can charge a cell phone — and plugged it into a new computer, he was given “full access” to the device and could control it from his phone.
“Never trust a cable that’s not yours,” he warned in the Instagram Reels video, which has scored 408,000 views.
Instead, he advised, in order to ensure data protection, to purchase a USB data blocker, a small device that acts as a barrier between cables and your computer in order to prevent cybercriminals from accessing information or infecting the device.
Dubbed a “USB condom,” the small dongle, which is usually inexpensive, prevents data from passing through the cable while still letting the device’s battery charge.
There are, however, counterfeit data blockers on the market that can be used by cybercriminals, according to ZDNet. Despite looking real, the malicious device actually contains hardware that can steal information, download malware onto devices and be controlled via Wi-Fi, the outlet reported.
Authentic USB data blockers, however, have been touted as a godsend for travelers who use public charging stations, which are known as prime “juice jacking” locations.
Hackers take advantage of the free charging hubs at malls, airports and other public spaces, tampering with the kiosks in order to steal data from users’ devices.
“Juice jacking is basically a portable charger or a charger out there in the public that’s been designed to look real,” cybersecurity expert Jim Stickley previously told NPR.
“It will actually charge your phone, but it’s also either installing malware on your phone or stealing data off of your phone or other mobile device.”
Instead of utilizing publicly available charging ports, experts recommend carrying your own portable battery pack, plugging your charger into a wall socket or using a USB data blocker.




